Archive
Trusted Platform Modules
If you are like me and use windows (among other operating systems), you might have wondered why M$ has required you to obtain new hardware just to run Windows 11. Is this just a cash grab by a greedy vendor or is there method to the madness after all?
The truth is, the industry has learned the costs of poor security, after decades of breaches and a patch routine that seems to never end. Created to help solve the problems associated with 2 factor authentication and now expanded to replace passwords altogether (using Passkeys), WebAuthN is an API specification designed to use public key cryptography to authenticate Entities (users) to relying parties (Web Servers).
Shown below (from the Yubikey site) demonstrating external authenticators (like Smart cards or hardware) or by utilizing Trusted Platform Modules in our devices, people can authenticate with (or without) the standard username and password we have been using for decades.
The idea of using a password has been like ‘leaving your front door key under the mat’. Anyone observing your behavior or just walking up and checking ‘under the mat’, can use it for themselves. Password abuse has become a leading cause of fraud to so many users that we started to send 6-8 digit codes via mobile telephone, so that users can authenticate using a second factor (2FA). Not everyone carries a mobile phone and we have learned that receiving these codes is not very secure because they are prone to interception.
We have relied on digital communications for e-commerce sites using cryptography (TLS) with such great success. Contributors like Google, Microsoft and many others decided that it was time to apply these principles to authentication and a specification was born.
The WebAuthN API allows servers to register and authenticate users using public key cryptography instead of a password. It allows web servers to integrate with the strong authenticators (using external ones like Smart cards or YubiKeys) and devices with TPMs (like Windows Hello or Apple’s Touch ID) to hold on to private key material and prevent it from being stolen by hackers.
Instead of a password, a private-public keypair (known as a credential) is created for a website. The private key is stored securely on the user’s device; a public key and randomly generated credential ID is sent to the server for storage. The server can then use that public key to prove the user’s identity. The fact that the server no longer receives your secret (like your password) has far-reaching implications for the security of users and organizations. Databases are no longer as attractive to hackers, because the public keys aren’t useful to them.
A virtual TPM is a software-based implementation of the same hardware-based TPM found in devices today. These vTPMs can be configured to simulate hardware-based TPMs for many operating systems. The Trusted Platform Group has created a standard but it is woefully outdated. Happily, many vendors have implemented the ability to use a vTPM in the last few years that allow us to implement external KMS systems to help protect them.
The cloud providers now support virtual TPMs for use with Secure Computing and Hypervisor support using your existing KMS solutions (KMIP). Even VMWare added its own Native Key Provider.
With support for newer operating systems that can take advantage of a TPM to protect private keys (even from its owner), the idea of Public Key Authentication provides users with the ability to eliminate passwords entirely while binding the authenticators to the people who need to use them rather than the hackers who don’t!
HyperV 2012 R2 preview
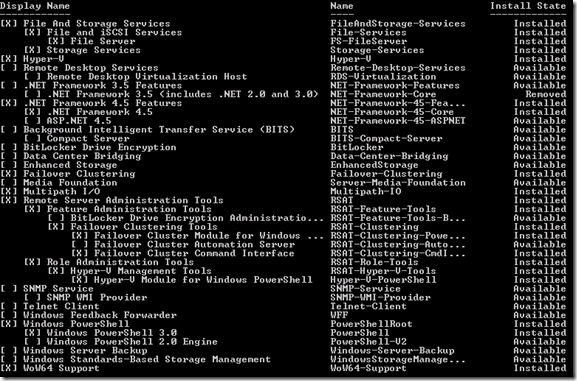
Its been over a year now and as soon as Microsoft put out the newest version of HyperV (Windows Hyper-V 2012 R2) I decided to give it a try. There was a new WMI namespace that promised to bring a heap of features to HyperV that would rival the other virtualization platforms and I was eager to get them working in the Lab. Unfortunately it might have been a bit premature but more on that later.
After reinstalling (MS suggests it and I had an error when I tried to upgrade from my HyperV 2012 hosts so I was forced to install a fresh copy),
After I installed the RSAT for Windows 8.1 I encountered some problems connecting to the HyperV options from my Windows 8.1 workstation using the HyperV manager but I was not immediately alarmed. I also noticed that I could not connect to my older system (Windows HyperV 2012) and chalked it up to the new WMI Namespace issue (Windows deprecated the older V1 namespace in the new versions of Windows 8/2012 R2).
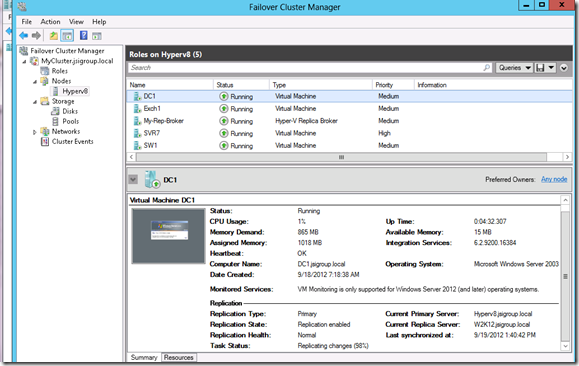
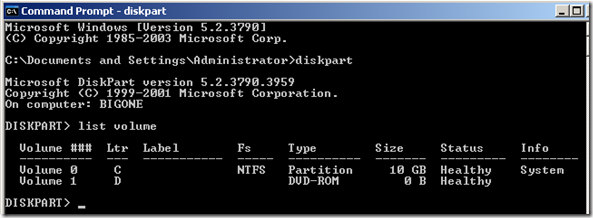
After following the lessons learned in the previous post here I was able to create my new Cluster using the following powershell command on one of the HyperV hosts.
‘New-Cluster -Name JSI-1 -Node HyperV1,HyperV2 –NoStorage’
I could then create my new VMs and ISO directories on the Clustered Shared Volume and start recreating my VMs.
‘New-VM -Name SW1 -Path C:\ClusterStorage\Volume1\VMs –Memory 512MB –SwitchName “New Virtual Switch”’
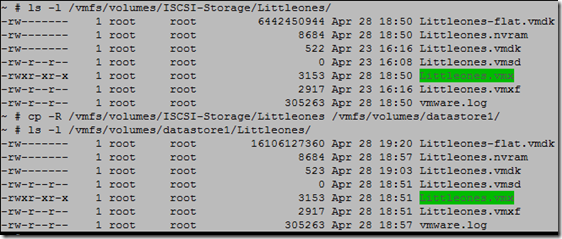
After all my vms directories were created I uploaded my vhd files to add to my VMs. (I decided to convert them to vhdx because they continue to use this new resilient image format introduced in 2012).
‘Convert-VHD –Path C:\ClusterStorage\Volume1\VMs\SW1\SW1.vhd –DestinationPath C:\ClusterStorage\Volume1\VMs\SW1\SW1.vhdx’
I was now ready to add my newly created vhdx files to my existing VMs and finally to spin them up.
‘ADD-VMHardDiskDrive –VMName SW1 -Path C:\ClusterStorage\Volume1\VMs\SW1\SW1.vhdx’
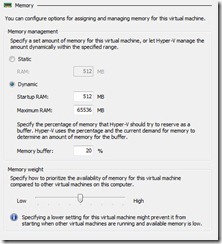
and finally let’s setup the dynamic memory feature like so…
‘Set-VMMemory –VMName SW1 -DynamicMemoryEnabled $True -MaximumBytes 1GB -MinimumBytes 256MB -StartupBytes 512MB’
Now let’s start that bad boy and get it back online…
‘Start-VM –name SW1’
(Here are the all of the commands for HyperV now for 8.1 and 2012 R2)
All is well again – well maybe not…
At the time of this writing there were all types of connection problems with the GUI tools. Windows 7,8,8.1 didn’t connect properly and even the Cluster Administrator with a newly installed Windows 2012 R2 server didn’t fully function. Powershell on the Hyper-V box was the only thing that worked properly – thank god for Powershell.
Maybe the GUI tools will mature after I write this article…
I mean after all it is Windows right ![]()