Archive
Giac Certifications are very difficult
Hi Everyone;
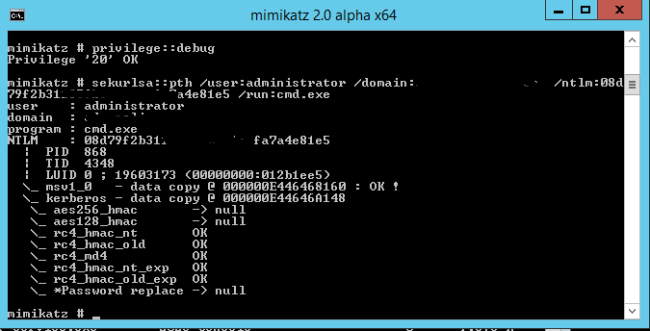
I wanted to share my experience recently regarding the GIAC Incident Handlers course (SEC-504). After almost 20 years in this business and years of experience with both Linux and Windows based systems it was some of the hardest studying I have done in a long while. It tested all of my fundamental knowledge – some gleaned from those years and years in the field. Most of the kudos goes to the course material – the books are the only thing you are allowed into the exam room with but the podcasts and the online slides and audio really helped me fit all of this educational curricula into what is already a challenging field. I hope to utilize a lot of this practical knowledge in the not to distant future using honey pots in my own lab. I sincerely hope that none of you get ‘pwned’ anytime soon but if you know of anyone in the GTA that has need for a certified incident handler – I would like to hang out my shingle.