Warning! Proceed with caution ⚠
Culture is more important than money (but I do need to pay my bills).
If you are not lucky enough to work for a company that you value or one that values you, learn about a bold approach to employment where they only want the best and try to tell yourself that you wouldn’t want to work there…
Kubernetes – steady as she goes
Looks like the fine folks running the Kubernetes core have the results from an audit they did. As many of the infrastructure teams look to use this code to help manage clusters of computing resources, we would all benefit from learning what could possibly go wrong 😊.
Many of the recommendations in the report involve code clean-up, adding further testing and documentation, and making defaults more security conscious.
These basic recommendations would make it easier to patch and resolve problems when they are found.
It is important to note that there were five “high severity” findings that included problems with access control, authentication, timing, and data validation.
Here is a look at the big ones…
- An access control bypass of PodSecurityPolicy
- K8s does not facilitate certificate revocation
- HTTPS connections are not authenticated
- Time of check, time of use problem with moving PID
- Improperly patched directory traversal in kubectl cp
Keep in mind that some of these have already been resolved if you are already using 1.15 branches.
The report is definitely worth a read and can be found here.
Black Hat USA 2019: IBM X-Force Red Reveals New ‘Warshipping’ Hack To Infiltrate Corporate Networks
Imagine, shipping a disposable package to someone at the office in order to gain access to a phone, test lab or even the corporate wifi network?
It is now a reality and can be done for less than $100 bucks (shipping charges may apply)
Are you sure you don’t want a Capital One card now?
In one of the largest breaches that affects over 6 million Canadians and potentially 100 million US customers, Capital One has revealed that it lost customer data and it was related to Security Misconfiguration. A suspect has been arrested, charged with computer fraud and abuse.
https://globalnews.ca/news/5700226/capital-one-data-breach-canada/amp/
Goodbye Docker: Purging is Such Sweet Sorrow – zwischenzugs
Now that IBM has thrown its hat in the cloud with the $34B purchase of Redhat, you should expect more innovation. This article from another WordPress site helps answer the question of why running docker is not necessary to have containerized solutions. You can minimize the attack surface and remove docker by using open source tools available to use today. https://zwischenzugs.com/2019/07/27/goodbye-docker-purging-is-such-sweet-sorrow/amp/
New European rules for mobile banking apps coming to a device near you…
The world is clearly a better place now that we carry computers in our back pocket but we need an increase in security measures for payment transactions and therefore we will require an increase in regulation, such as the PSD2 from European Commission.
The Payment Services Directive mandates compliance by September 2019 and aims to regulate banks, payment service providers and electronic payments to include security features to protect consumers across digital channels. The PSD2 legislation will require financial services in the European Union (EU) to contribute to a more integrated, secure, and efficient payments ecosystem.
The PSD2 directive requires financial institutions to:
- Provide/Implement a monitoring mechanism in their apps to detect/report signs of malware.
- Provide security measures in their app to mitigate risk for the user device.
- Ensure consumers have a secure environment to execute their financial transactions
In Article 2 and Article 9 of the directive, PSD2 highlights Strong Customer Authentication (SCA) and Safe Execution Environment (SEE), which requires de-risking across various threat vectors impacting mobile apps.
These include detecting compromised devices (eg: jailbroken or rooted), unsafe environments (such as a fake or malicious wi-fi), as well as malware and vulnerabilities within the application execution environment. PSD2 also includes RTS (Regulatory Technical Standards), which are regulatory requirements set by the European Banking Authority (EBA) to ensure that payments across the EU are secure, fair & efficient.
To meet these requirements, financial institutions should add strong security capabilities like binary protections to their mobile apps. These controls are designed to protect against known and unknown threats on users’ devices.
Mobile banking apps should also be able to detect when they are installed on risky devices and consider restricting access to high value banking services until those risks have been remediated.
Honest, it was like that when I drove up?
It can be comforting to know that McD’s is still running Windows XP for their drive up kiosks…
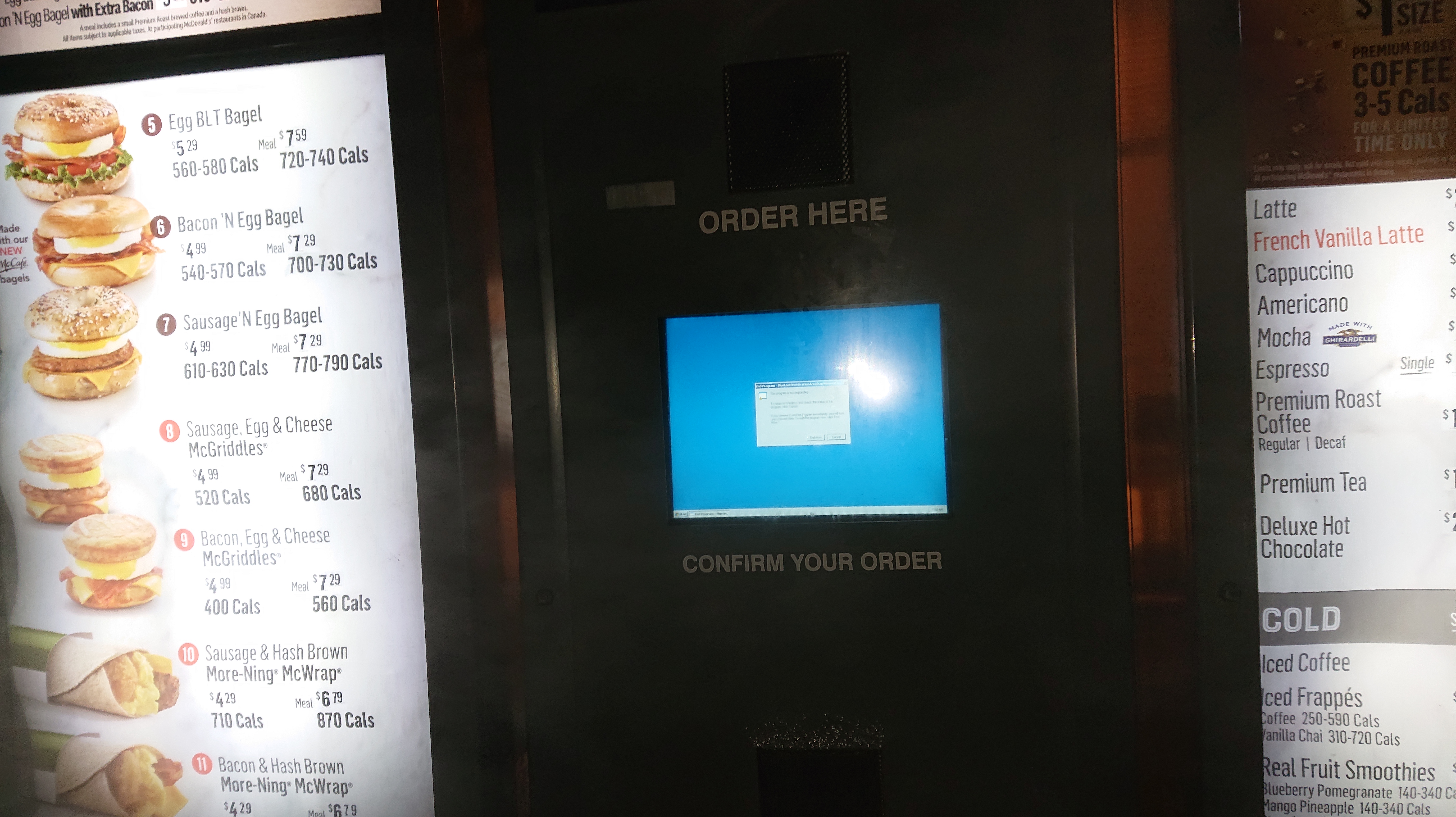
and is still having logic based software problems like the rest of big enterprise isn’t it?
WebInspect has 3 great new features – Micro Focus Community – 1796294
Malicious Python libraries targeting Linux servers removed from PyPI | ZDNet
3 malicious libraries used in many open source packages. https://www.zdnet.com/google-amp/article/malicious-python-libraries-targeting-linux-servers-removed-from-pypi/