Archive
Why exfil your payload via ASCII? A picture is worth…
Malwarebytes has discovered a new type of skimming attack where the booty is sent via an image!
The attackers hides the credit card skimmers in the metadata of icon files and then sends the sensitive info after the attack is successful, to the C2 via an image.
Talk about the need for ‘copy protection’?
As if hiding JavaScript in the copyright tag of the ico file isn’t ingenuous enough, they capture input field data, obfuscate it and place it in a image file to be uploaded so your Siem doesn’t even see it?
They have shared the details in a blog post if you want to learn more.
https://latesthackingnews.com/2020/07/06/attackers-hide-credit-card-skimmers-in-image-files-to-steal-data/
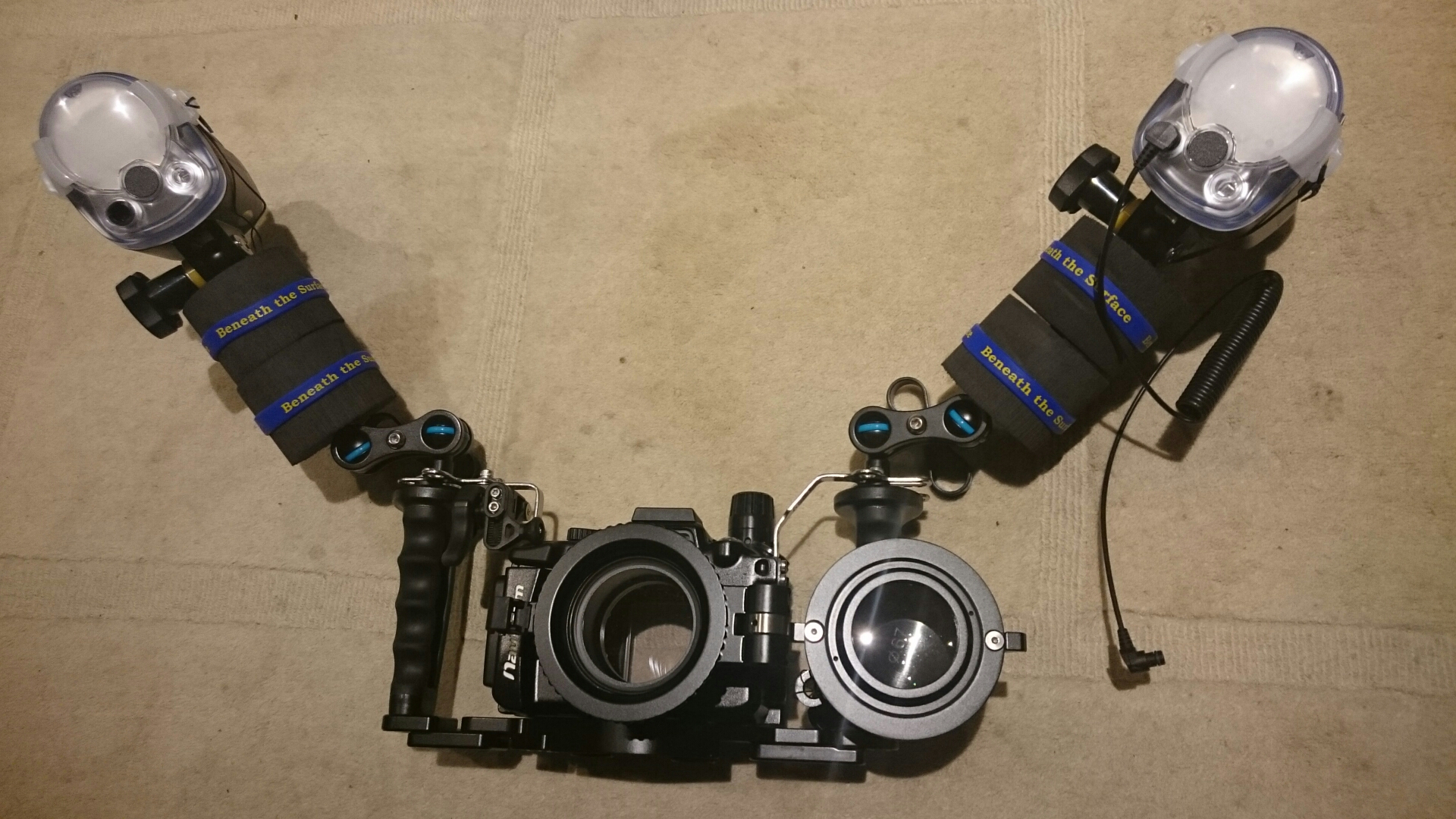
Getting ready to take more underwater pictures
I got another strobe and a new macro lens for our underwater rig today. Can’t wait to take some great pictures in Florida. Check out the flip mount for our diopter…